Heartbleed
Heartbleed is a security bug disclosed in April 2014 in the OpenSSL cryptography library, which is a widely used implementation of the Transport Layer Security (TLS) protocol.
(TO DO: expand, organize, cross-reference, illustrate.)
Contents
Description
Heartbleed may be exploited regardless of whether the party using a vulnerable OpenSSL instance for TLS is a server or a client.
It results from improper input validation (due to a missing bounds check) in the implementation of the TLS heartbeat extension, thus the bug's name derives from "heartbeat".
The vulnerability is classified as a buffer over-read, a situation where more data can be read than should be allowed.
Heartbleed is registered in the Common Vulnerabilities and Exposures system as CVE-2014-0160.
The federal Canadian Cyber Incident Response Centre issued a security bulletin advising system administrators about the bug.
A fixed version of OpenSSL was released on April 7, 2014, on the same day Heartbleed was publicly disclosed.
At the time of disclosure, some 17% (around half a million) of the Internet's secure web servers certified by trusted authorities were believed to be vulnerable to the attack, allowing theft of the servers' private keys and users' session cookies and passwords.
The Electronic Frontier Foundation, Ars Technica, and Bruce Schneier all deemed the Heartbleed bug "catastrophic".
Forbes cybersecurity columnist Joseph Steinberg wrote, "Some might argue that [Heartbleed] is the worst vulnerability found (at least in terms of its potential impact) since commercial traffic began to flow on the Internet."
Randall Munroe explains
Randall Munroe, author of xkcd, explains Heartbleed like this:
How it works
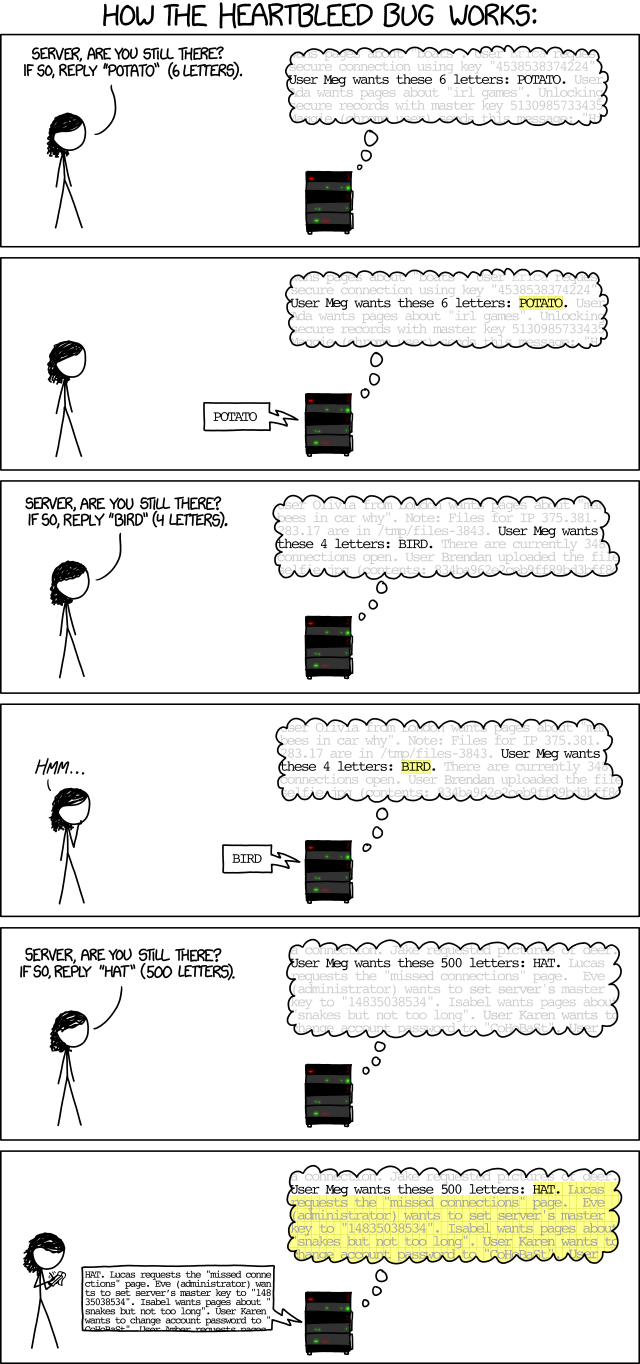
Source: Heartbleed Explanation
The consequences

Source: Heartbleed
See also
External links
- Heartbleed @ Wikipedia